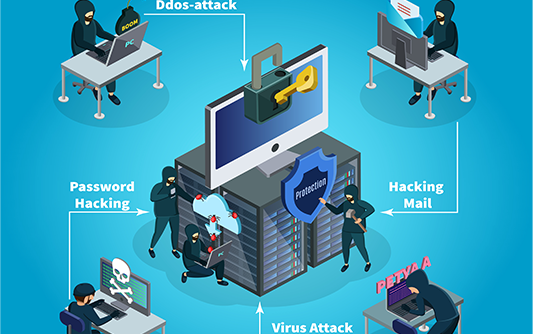
Yes, threats are increasing exponentially in sophistication, intensity, diversity and volume. Cyber experts report significant escalation in external cyber attacks, especially from criminal organizations and foreign state sponsored activities.
Mobile devices do bring great utility in terms of convenience and allowing individuals to be “online all the time.” Governments have widely deployed mobile devices for accessing resources and greater workforce productivity. However, the use of mobile devices for communicating and for sharing data create inherent security issues and add more points of access to the network.
Even as CISOs better define their roles and become an integral part of state government, they continue to face challenges, particularly in securing the resources they need to combat ever-evolving cybersecurity threats. Four-fifths (80 percent) of respondents say inadequate funding is one of the top barriers to effectively address cybersecurity threats, while more than half cite inadequate availability of cybersecurity professionals
Cyber security will require funding for creating the necessary capabilities that include tools and training for cyber security. However, cyber security must be “baked into” every project, program and management initiative – and not be an administrative afterthought. Cyber security must be understood as an inherent cost of doing business and must be a component of every budget.
security – but they don’t know enough to protect themselves. Most people may People know about cybereven understand the imperative for protecting data and the fact that cyber threats are getting worse. However, effective cyber security is an ongoing maturing capability for not only the government enterprise but for individuals who are employed by or served by state government. This capability must be continually exercised, tested and strengthened through awareness training to not only combat aggressive cyber threats, but also accidental, unintentional cyber events.
Yes. Cloud services promise to provide flexibility, scalability, measured service and certain cost efficiencies, but also present additional security risks associated with authentication, access and storage of government data. The total economic cost and different security elements of cloud services must be fully understood when evaluating cloud computing in general and the various deployment models (public, private, hybrid, community). Consumer-based cloud services used by government workers present additional risks because they may not offer rigorous security controls.